
ACC Demystified: Your Ultimate Security Guide
What Exactly is ACC?
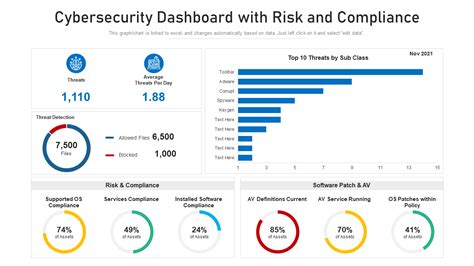
In the ever-evolving digital landscape, ACC (Access Control) stands as a critical pillar of cybersecurity. At its core, ACC determines who can view or use resources in a computing environment. Think of it as the digital bouncer for your sensitive data, applications, and infrastructure. Without robust access controls, organizations leave themselves vulnerable to breaches, data leaks, and compliance violations.
Why ACC Matters More Than Ever
Recent cyberattacks targeting major corporations highlight the devastating consequences of weak access management. When unauthorized users gain entry, the fallout can include:
- Data theft of customer information
- Ransomware deployment crippling operations
- Regulatory fines for non-compliance
Effective ACC implementation creates a zero-trust architecture where every access request is verified, regardless of origin.
Key Components of Modern ACC Systems
Today's ACC solutions combine multiple technologies:
"Multi-factor authentication is no longer optional – it's the baseline expectation for secure access."
- Identity Management - Verifying user identities
- Authentication - Validating credentials (passwords, biometrics)
- Authorization - Defining access permissions
- Audit Logging - Tracking all access attempts
Emerging ACC Trends to Watch
The ACC landscape continues to evolve with these innovations:
- Biometric Integration - Facial recognition and fingerprint scanning
- AI-Powered Anomaly Detection - Identifying suspicious patterns
- Zero Trust Architecture - Continuous verification protocols

Best Practices for Implementation
Organizations should follow these ACC fundamentals:
- Implement role-based access controls (RBAC)
- Enforce strong password policies
- Regularly audit user permissions
- Train employees on security awareness
Remember, access control isn't a one-time setup—it requires ongoing maintenance and updates to address new threats.
The Future of Access Control
As quantum computing and IoT devices proliferate, ACC systems must adapt. Future solutions will likely leverage blockchain for immutable access logs and behavioral analytics to predict potential breaches before they occur.
Conclusion
ACC remains your first line of defense in the digital realm. By understanding its principles and implementing best practices, organizations can significantly reduce their attack surface while maintaining operational efficiency.
Share this article
Sarah Johnson
Technology journalist with over 10 years of experience covering AI, quantum computing, and emerging tech. Former editor at TechCrunch.